Securing a Portal Experience with SSL
Secure Sockets Layer (SSL) is the standard security technology for establishing an encrypted link between a web server and a browser. This link ensures that all data passed between the web server and browsers remain private and integral. SSL is an industry standard and is used by millions of websites in the protection of their online transactions with their customers.
Notes on using SSL with Gallery
- Publishers are responsible for the SSL certificate
- Self-signed certificates are not supported
- The private key cannot be encrypted with a password
- The private key should start and end with ‘-----BEGIN RSA PRIVATE KEY-----’ and ‘-----END RSA PRIVATE KEY-----’
- The maximum SSL certificate key length supported by Gallery is 2048 bits
- Brightcove requires the certificate to be in PEM format
- Brightcove recommends that SSL certificates used in Gallery sites not be used anywhere else
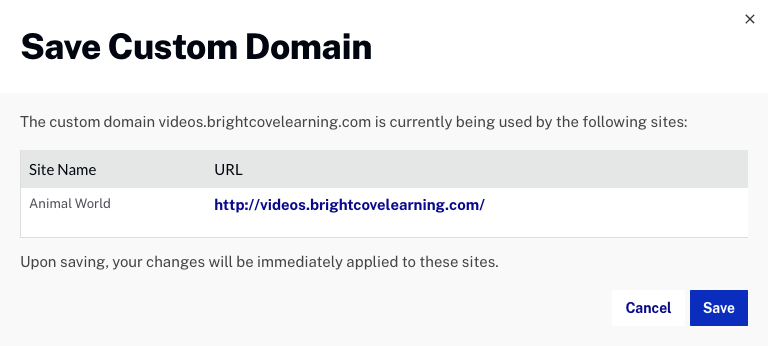
- Publishers must use a custom domain name
Configuring a Portal Experience for SSL
These steps assume you have purchased an SSL certificate. Your video site must also be configured to use a custom domain. For information on configuring a site to use a custom domain, see Configuring Custom Domains and SSL.
Upload the SSL certificate
- Open the Gallery module.
- Click the settings icon (
 ) on the home page.
) on the home page. - In the left navigation, click the Custom Domains & SSL link.
- Edit the custom domain that SSL will be enabled for.
- Check Use SSL.
- Paste in your Server Certificate. Remove any blank lines at the beginning or end of the key. Brightcove requires the certificate to be in PEM format.

- Paste in your Server Private Key. Remove any blank lines at the beginning or end of the key. Brightcove requires the certificate to be in PEM format.

- Paste in your Chain of CA Certificates. If your certificate was signed by a root CA, then only the root certificate CA needs to be pasted in. This should not include your own certificate. The certificate order is immediate cert. > any other intermediary > root (the root certificate is optional).
Remove any blank lines at the beginning or end of the key. Brightcove requires the certificate to be in PEM format.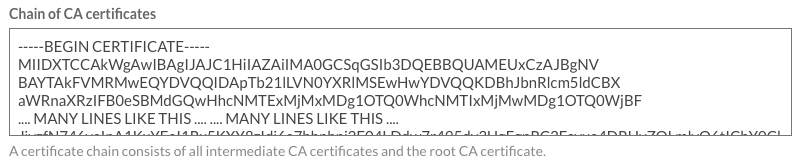
- Click . The site details will be displayed.
- Click . The certificate will be validated and if there are errors, they will be displayed.
The SSL status will display Updating Configuration while the SSL information is being updated and propagated. Click Refresh List to update the SSL status.
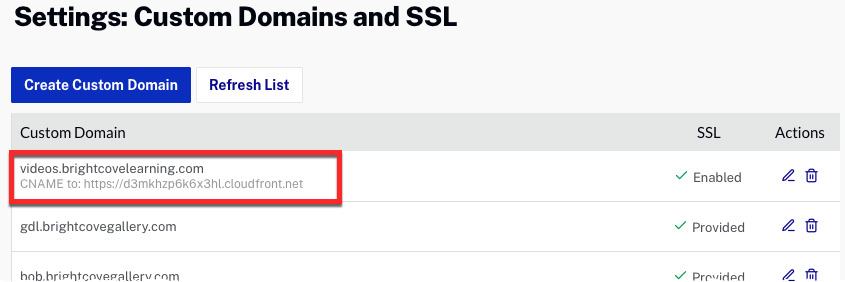
Configure the CNAME record
Once SSL has been configured, the SSL status will be Enabled. The CNAME information will be updated with a CloudFront URL. The CloudFront URL will not change unless the domain is deleted.
Note that browsing directly to a CloudFront URL will return a "page not found" error (404). A curl command can be used to verify the domain configuration. For this example:
curl -H "Host: video.brightcovelearning.com" https://d3mkhzp6k6x3hl.cloudfront.net
The curl statement should return the contents of the site home page.
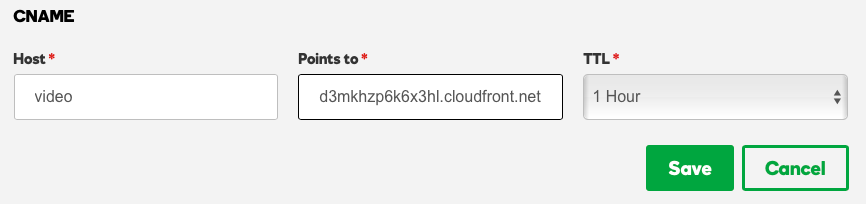
The CNAME record for your custom domain should redirect to the CloudFront URL displayed on the Custom Domains and SSL page.
Updating/Replacing SSL certificates
If an SSL certificate needs to be updated or replaced, for example, the SSL certificate may be set to expire, follow these steps to replace an existing SSL certificate.
- Open the Gallery module.
- Click the settings icon (
 ) on the home page.
) on the home page. - In the left navigation, click the Custom Domains & SSL link.
- Locate the custom domain using the SSL certificate and then click the edit icon (
 ).
). - Click Upload new certificate.
- Paste in the new Server Certificate, Server Private Key and Chain of CA Certificates. Remove any blank lines at the beginning or end of the keys.
- Click .
If there are any errors with the updated keys, the old values will be retained.
Sample keys
Below are examples of some sample certificates/keys.
Sample server certificate
-----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBFA .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA== -----END CERTIFICATE-----
Sample server private key
-----BEGIN RSA PRIVATE KEY----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA= -----END RSA PRIVATE KEY-----
Sample chain of CA certificates
-----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA== vA== -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF .... MANY LINES LIKE THIS .... .... MANY LINES LIKE THIS .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpRC3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPULB7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq vA== vA== -----END CERTIFICATE-----
Sample certificates
Sample public key
-----BEGIN RSA PRIVATE KEY-----
MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX
aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF
A .... MANY LINES LIKE THAT .... .... MANY LINES LIKE THAT ....
JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpR
C3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPUL
B7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq
vA==
-----END RSA PRIVATE KEY-----
Sample server private key
-----BEGIN RSA PRIVATE KEY-----
MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX
aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF
A .... MANY LINES LIKE THAT .... .... MANY LINES LIKE THAT ....
JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpR
C3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPUL
B7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq
vA==
-----END RSA PRIVATE KEY-----
Sample certificate chain
-----BEGIN CERTIFICATE-----
MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX
aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF
A .... MANY LINES LIKE THAT .... .... MANY LINES LIKE THAT ....
JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpR
C3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPUL
B7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq
vA==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX
aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF
A .... MANY LINES LIKE THAT .... .... MANY LINES LIKE THAT ....
JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpR
C3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPUL
B7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq
vA==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm5ldCBX
aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OTQ0WjBF
A .... MANY LINES LIKE THAT .... .... MANY LINES LIKE THAT ....
JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3UgEgpR
C3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL2JlPUL
B7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYcm0A6Jq
vA==
-----END CERTIFICATE-----
Troubleshooting
Troubleshooting SSL certificate installations requires quite a bit of attention to detail. As you see above, there are several names and words that mean the same but are in different places. There are a few 'Gotchas' that may help though.
SSL Certificate Issues/Install Issues:
- Is the Domain's CNAME Correct?
(TL;DR: It should be pointed to a CloudFront URL and not the bcvp0rtal address.) Did you update the CNAME for their domain name to point to the new URL? When you add an SSL to Gallery, it migrates the site to a CloudFront URL with HTTPS accessibility over a custom domain name. The CNAME needs to be updated at the Domain's DNS level in order to resolve.
Gallery Site CNAME Lookup Amazon CloudFront CNAME and HTTPS requirements
- Is this a Self-Signed Certificate?
- Is the certificate valid yet/or expired?
- Is the Custom Gallery Domain Present?
- Are the certificates in the right order?
- Is the Certificate at least SHA256?
- Does the Certificate include the header and footer?
- SSL installed, but the site isn't working?
e.g. Is there an Issuer and is that Issuer Valid?
It's common for publishers to renew certificates and sometimes may have a new copy that isn't valid yet or an old copy that's expired.
Be sure to check the Common name on the server certificate as well as the SANs. It doesn't have to be in both, but it does have to be in at least one of them.
It's good to make sure the Chain certificates are in the box and the public key is in the right box. Sometimes can send the certificate and the chain certificates (NOT the private key), you can use SSL Shopper to get them in the right order. (Open them with a text editor to see the certificate itself).
This is important, Gallery is not compatible with SHA128 anymore, so the Certificate needs to be at least SHA256. But you may also encounter a SHA512, which can be used as well.
This is imperative, it should begin and end with 5 hyphens.E.g. -----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----If you see -----BEGIN PRIVATE KEY----- the certificate should be compromised.
Do they have any external objects or scripts on the site? If so, are you using HTTP? Are you on an HTTPS-accessible CDN? EVERYTHING on an SSL site needs to be HTTPS or it will break, browsers are becoming more strict about this too. Even consider the player and its plugins.
DNS and Website Issue:
- Is the website still saying HTTPS is broken, even though the certificate is installed?
Did you update the CNAME for their domain name to point to the new URL? When you add an SSL to Gallery, it migrates the site to a CloudFront URL with HTTPS accessibility over a custom domain name. The CNAME needs to be updated at the Domain's DNS level in order to resolve. Typically this can take up to 6 hours or so to completely show up, but usually will be online within 30 minutes (after clearing cache, cookies, and restarting your browser). You can confirm what's showing publicly for the domain itself by using "dig" in the command line. Alternatively, if you're not so command-line oriented you can use Dig Web Interface to see what the domain is showing.
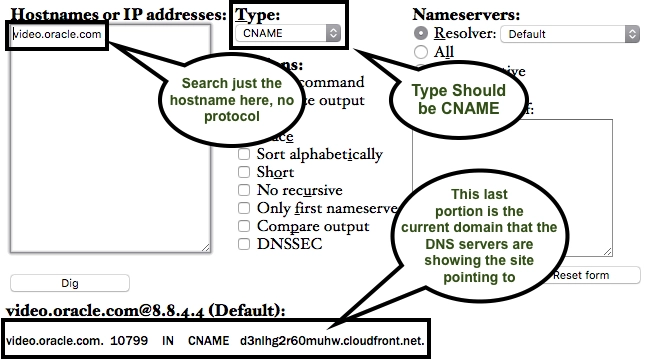
Above is a functioning Gallery website, using a custom domain name and SSL certificate. You can see it changed from the traditional site-slug to the CloudFront address, if you're not seeing this in your browser, it's either Browser or DNS cache on your end, but this shows what the DNS currently shows directly for the site.
- Copy/Paste issues come into play here as well
- Propagation is important to remember
- HTTPS showing broken on the site, but the site still works?
Be sure to double check the CNAME within the Gallery's settings in order to make sure everything is the same. (You can use CTRL+F to confirm everything is the same).
DNS changes can be instant sometimes, but most of the time they take time to change over. Some DNS providers quote upwards of 72 hours for this process to occur, but in reality, it's more like 30 to 120 minutes. ISPs commonly refresh DNS cache and provided you're maintaining good browser health it will show up relatively quickly.
This is more than likely due to something added onto the page or the player that's specifically using HTTP. All plugins for the player should be protocol agnostic (e.g. //players.brightcove.com), but sometimes there are cases of specify a hard protocol either HTTP or HTTPS, HTTPS wouldn't be an issue in this case, but HTTP would cause a hard stop. It may not break the site entirely, but it does break the certificate and the chain behind it, which leaves an ugly view to a user.
SSL Troubleshooting Continued
To learn more about the basic requirements for SSL, see Securing a Portal Experience with SSL
The following content dives a little deeper into how to troubleshooting. The error displayed when a certificate upload fails is: The SSL certificate information you provided failed validation. Please check your certificate and try again. This could possibly mean multiple issues and here are the steps, in order of what might cause them:
- The keys were copied incorrectly
- Probably was not copied the full key ie. the ‘-----BEGIN CERTIFICATE-----’ and ‘-----END CERTIFICATE-----’ were not included
- The public key should start and end with ‘-----BEGIN CERTIFICATE-----’ and ‘-----END CERTIFICATE-----’ respectively
- The private key should start and end with ‘-----BEGIN RSA PRIVATE KEY-----’ and ‘-----END RSA PRIVATE KEY-----’
- If it does not start with BEGIN RSA PRIVATE KEY, then the key might be exported in another format than RSA. Gallery only accepts RSA Private Key as outlined in Cloudfront: Requirements for using SSL/TLS certificates with CloudFront.
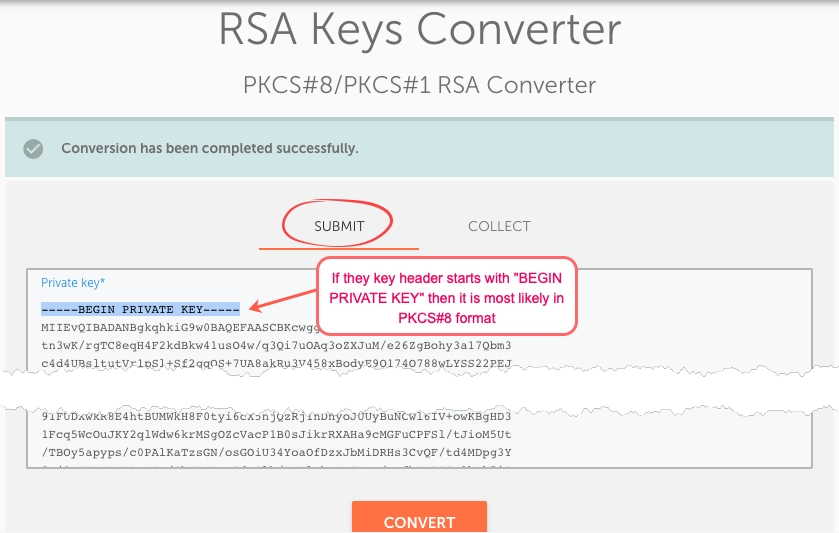
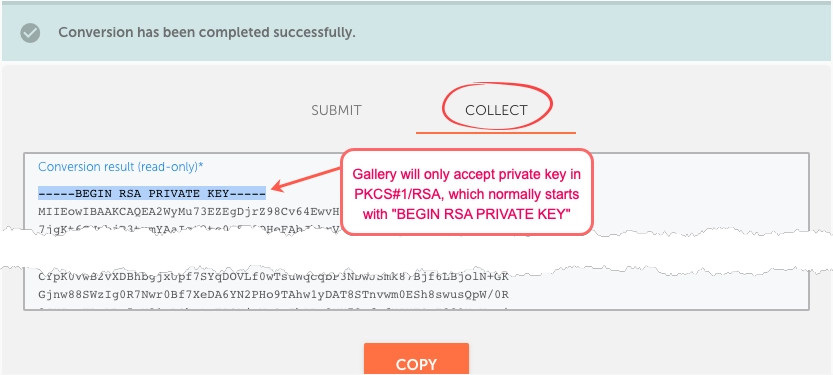
- The certificate chain can have multiple concatenated keys.
- The key is not in PEM format
- The key was self-signed
- The private key is password protected
- The certificate chain is not in the right order. Sometimes you receive an email with separate certificates (Root CA, Intermediate, UserTrust) for the chain cert and try to manually combine them together. If this happens: You can use this tool to check if the order of the certificates in the chain is correct: Certificate Checker
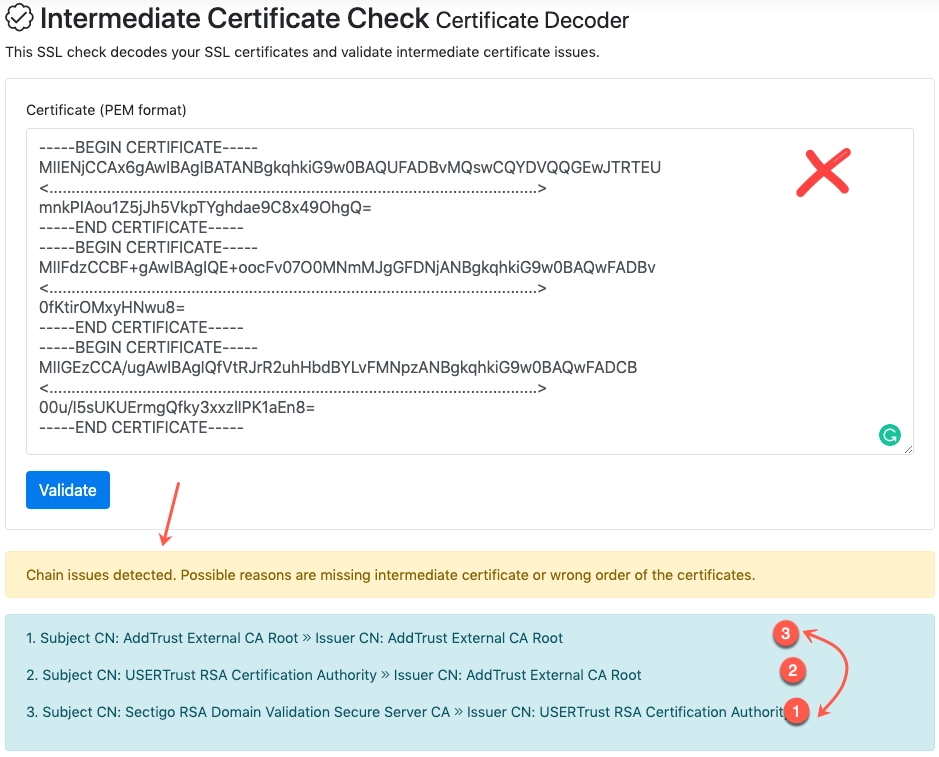
Check with the issuer of the certificates.
Check with the issuer of the certificate.
We do not support password protected private keys.
Non-password protected keys will look like:
2. -----BEGIN RSA PRIVATE KEY----- 3. MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCz AJBgNV 4. BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm 5ldCBX 5. aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OT Q0WjBF A 6. .... MANY LINES LIKE THAT .... .... MANY LINES LIKE THAT .... 7. JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3 UgEgpR 8. C3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL 2JlPUL 9. B7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYc m0A6Jq 10. vA== -----ENDBEGIN RSA PRIVATE KEY-----
Whereas password protected keys will look like this:
-----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: DES-EDE3-CBC,91B305001070B5FD MIIDXTCCAkWgAwIBAgIJAJC1HiIAZAiIMA0GCSqGSIb3DQEBBQUAMEUxCz AJBgNV BAYTAkFVMRMwEQYDVQQIDApTb21lLVN0YXRlMSEwHwYDVQQKDBhJbnRlcm 5ldCBX aWRnaXRzIFB0eSBMdGQwHhcNMTExMjMxMDg1OTQ0WhcNMTIxMjMwMDg1OT Q0WjBF A .... MANY LINES LIKE THAT .... .... MANY LINES LIKE THAT .... JjyzfN746vaInA1KxYEeI1Rx5KXY8zIdj6a7hhphpj2E04LDdw7r495dv3 UgEgpR C3Fayua4DRHyZOLmlvQ6tIChY0ClXXuefbmVSDeUHwc8YufRAERp2GfQnL 2JlPUL B7xxt8BVc69rLeHV15A0qyx77CLSj3tCx2IUXVqRs5mlSbq094NBxsauYc m0A6Jq vA== -----ENDBEGIN RSA PRIVATE KEY-----
After changing the order and removed the third:
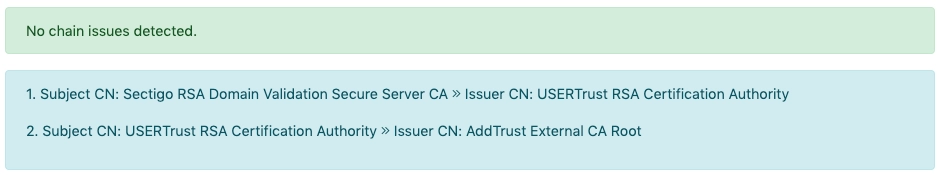
- Search for a publicly available certificate chain bundle from the issuer.e.g.: If it's from Sectigo How to Download & Install Sectigo Intermediate Certificates - RSA
- Most chain bundle has 2 certificates. Check if gives you a bundle with 3 certs Intermediate certificates
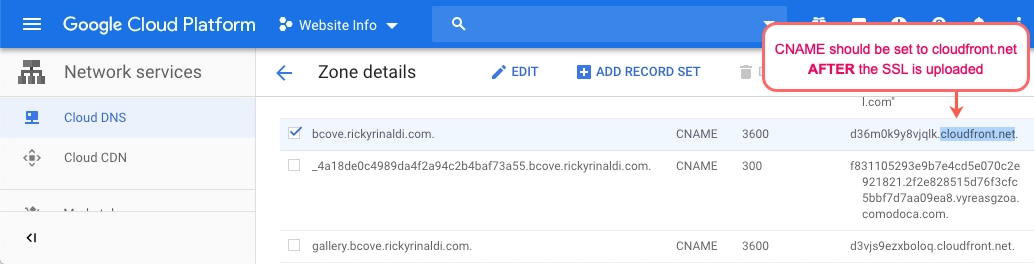
- Check the CNAME of the domain name is pointing to a Cloudfront site instead of bcvp0rtal.com. Please check with MXToolbox to confirm if that is the case: SuperTool
If the console returns an error "Status Code: 409; Error Code: CNAMEAlreadyExists" then it means it has already set the sub-domain to CNAME to Cloudfront before the SSL is uploaded. Cloudfront CNAMEAlreadyExists: How do I resolve the CNAMEAlreadyExists error when I set up a CNAME alias for my CloudFront distribution? .
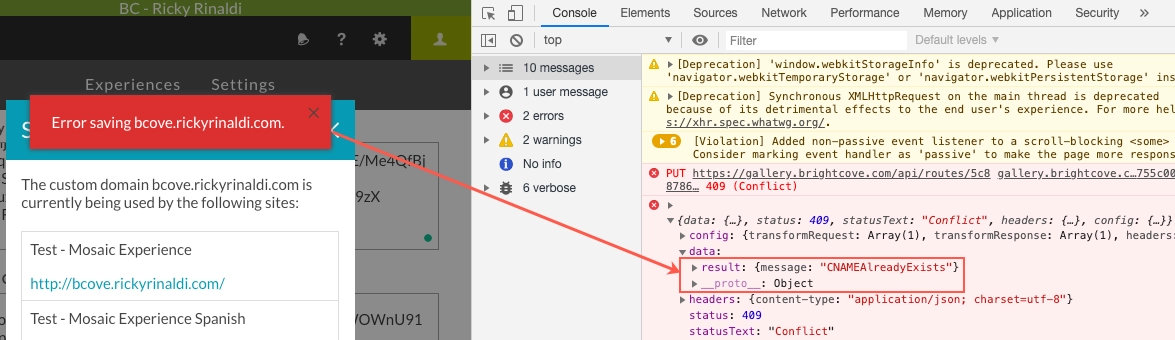
- To resolve this issue, delete the CNAME or put it back to "< gallery-site-id >.bcvp0rtal.com" in your DNS Zone manager and try to upload the SSL certificate again
- Incorrect line ending: If the key was transferred between a Linux and Windows machine, there is a very low chance that line ending got messed up. Read EditPad Pro
- The public key and private key don’t match: This is a rare case. In this case, the IT team should be brought in.
- Ping the Gallery team with the following information:
- Publisher ID
- Certificate issuer
- Timeframe when you tried to upload the certificate
- Answers to the above questions
